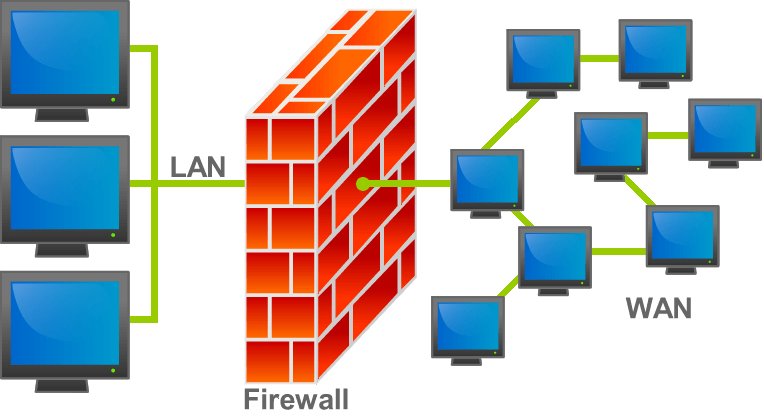
1.4.2 – Identifying and Preventing Vulnerabilities
In the previous section, 1.4.1 – Threats to Computer Systems and Networks, we looked at a fairly comprehensive rundown of the most common and prevalent […]

In the previous section, 1.4.1 – Threats to Computer Systems and Networks, we looked at a fairly comprehensive rundown of the most common and prevalent […]
Copyright © 2024 | WordPress Theme by MH Themes